Key Concepts
Authorization
Authorization is the act of allowing a user to access a resource. Access Control's primary function is authorization.
In Access Control, the resources are ArcGIS Server layers, fields, and features. The users and groups come from the security model that you use to secure ArcGIS Server:
-
Federated Security: Access Control gets the users and groups from the portal.
-
Windows Integrated Security: Access Control gets the users and groups from Windows.
-
Token Security: Access Control gets the users and groups from ArcGIS Server.
See also...
Proxy
Access Control's main component is a proxy that acts as a forwarding proxy for the ArcGIS Web Adaptor. The Proxy receives all the traffic to and from ArcGIS Server, regardless of its origin. For example, a request could come from Geocortex applications like VertiGIS Studio Web, VertiGIS Studio Workflow, or Geocortex Essentials, or from ArcGIS applications like Experience Builder, Web AppBuilder, or Collector.
When the Proxy receives a request, it decides what to do with the request based on the permissions and filters you have configured for the user. The Proxy could deny the request, let it go through as is, augment the query, or filter features from the response.
Permissions
A permission is a level of authorization to access a particular resource. As an Access Control administrator, your main task is to apply permissions to users and groups to ensure that users have access to just those resources they need.
Access Control has the following permissions:
-
 Visible permission allows the user to see the resource anywhere that it appears—in the service list, in the layer list, on the map, in search results, and so on.
Visible permission allows the user to see the resource anywhere that it appears—in the service list, in the layer list, on the map, in search results, and so on. -
 Editable permission allows the user to see and modify the resource.
Editable permission allows the user to see and modify the resource. -
 Denied permission prevents the user from seeing the resource in any context. From the user's point of view, the resource does not exist.
Denied permission prevents the user from seeing the resource in any context. From the user's point of view, the resource does not exist.
See also...
Access Control User Groups
VertiGIS Studio Access Control offers three built-in groups that supplement the groups provided by ArcGIS:
- Authenticated Users: Includes all users that are signed in
- Anonymous Users: Includes all users that are not signed in
- All Users: Includes both Authenticated Users and Anonymous Users
Inheritance
In VertiGIS Studio Access Control, permissions are inherited—from both the ArcGIS Server and from the parent service/layer.
Inheriting ArcGIS Server permissions
ArcGIS Server permissions control 'all or nothing access' to the service. VertiGIS Studio Access Control honors these permissions.
For example:
- If access is denied at the ArcGIS Server level, you cannot override this in the Access Control Designer.
- Users with the ArcGIS Server Edit permission for Feature Services and Read permission for Map Services will inherit these in Access Control. You can override these in the Designer and restrict or deny access.
Inheriting Access Control permissions
When you configure permissions in the Access Control Designer, you do not need to apply a permission to every layer and field.
By default, child elements (layers and fields) inherit permissions from the parent layer. Child permissions can override inherited permissions.
For example:
- If you deny access to a service, all layers or tables in the service inherit the Denied permission.
- If you deny access to a layer, all fields on that layer inherit the Denied permission.
- If you deny access to a group layer, all child elements inherit the Denied permission. If you subsequently apply a Visible or Editable permission to a child element, this will override the inherited permission.
Combining permissions and filters
For a given layer or field, multiple permissions and filters may apply. For example, multiple permissions/filters may be applied to the same user based on one or more of the following:
- The explicit user name of the user
- An ArcGIS Server group to which the user belongs
- The Authenticated Users Access Control group
- The Anonymous Access Control group
- The All Users Access Control group
Permission/filter inheritance is applied according to the list order specified above. For example, an explicit user name permission will override a competing group permission, and an ArcGIS Server group permission will override an Access Control user group permission. In other words, the more a permission specifically targets a user, the more weight that permission has.
When competing permissions/filters have equal weight (for example, you have both All Users: Allow and All Users: Deny permissions), the following rules apply:
- A Visible permission overrules Editable permissions.
- A Denied permission overrules both Visible and Editable permissions.
- A Denied permission overrules all attribute and geometry filters.
- When multiple attribute filters apply, only the first one listed in the Access Control Designer will be used. The attribute filters are not merged/joined.
- When multiple geometry filters apply, only the first one listed in the Access Control Designer is used. The geometries are not merged/joined.
- You can apply both attribute and geometry filters at the same time.
See also...
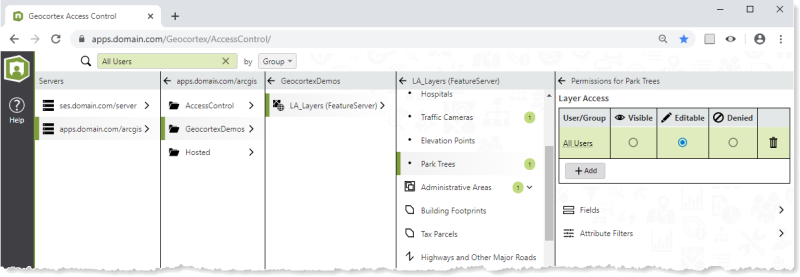
Access Control Designer
Access Control has a web-based Designer that you use to manage access to your organization's ArcGIS Servers. The Designer allows you to apply permissions to users and groups; define filters to restrict the features that users or groups can access; and search for and view the permissions for a particular user or group.
To sign in to the Designer, you must have an ArcGIS Administrator account.
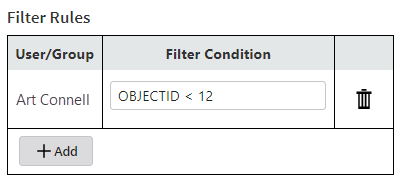
Filters
A filter is a WHERE clause that filters the rows in the data table based on attribute values. Filters allow you to control which features users can access.
To define a filter, you create a filter rule that applies a logical condition to a user or group. The condition defines the attribute values to allow the user or group access. For example, the attribute filter rule shown below allows the user Art Connell to only access features with OBJECTID less than 12.