Windows Authentication
Integrated Windows Authentication (IWA) uses Windows users and roles. IWA is appropriate for securing sites that will be used by members of your organization.
Windows Users and Roles
The Windows Integrated security provider allows you to apply permissions to the following types of users and roles:
-
Windows Integrated - All Users: Permissions that you set for All Users apply to all users who authenticate using their Windows credentials when they launch the viewer.
-
Windows Integrated - Windows Account: Permissions that you set for a particular Windows account only apply to that user account.
-
Windows Integrated - Windows Group: Permissions that you set for a particular Windows group apply to users that belong to that group.
Enable Windows Authentication
To use Integrated Windows Authentication for Essentials Security, Windows Authentication must be enabled. You can use the Post Installer to enable Windows Authentication. Turning on Windows Authentication in the Post Installer is equivalent to installing Windows Authentication in Internet Information Services (IIS) and enabling the Windows Authentication Windows feature.
To enable Windows Authentication using the Post Installer:
-
In the Post Installer, click Configure Windows Features in the side panel.
-
Select the Windows Authentication checkbox.
If the checkbox is selected and grayed out, Windows Authentication is already installed and enabled.
-
Click Finish.
You have now enabled Windows Authentication.
Windows Authentication with Active Directory
If you use Active Directory with Integrated Windows Authentication, Essentials automatically uses the Active Directory users and groups. To find a user or group, start to type in the name, and then select the user or group from the drop‑down list.
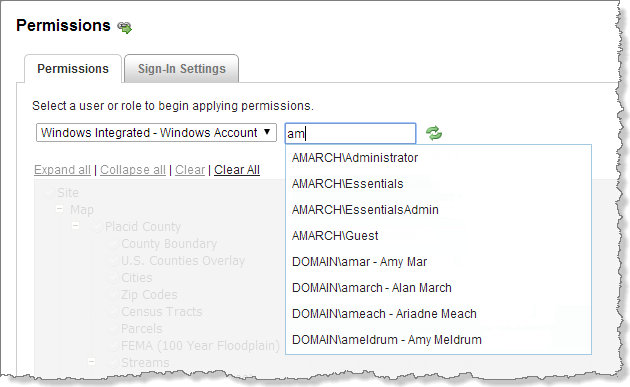
Example of accessing a Windows account from Active Directory
In addition to using Active Directory with Windows Authentication, you can use standalone Active Directory membership and role providers with Geocortex Identity Server. For information, see Geocortex Identity Server.
Single Sign-On
Integrated Windows Authentication supports single sign-on, which automatically signs in users using their Windows credentials.
In order for single sign-on to work, the user must already be signed in to Windows. In addition, the client browser's security settings must have automatic authentication enabled under the current user name and password, for the appropriate zone. If one or more of these conditions is not met, the user has to sign in.
For complete steps to set up single sign-on, refer to the Geocortex Knowledge Base article "Configure single sign-on with Essentials Manager and viewers".
If Windows Integrated is the only service provider that you are using, you may want to configure a landing page so the user's browser is directed to a different page after the user signs out. Otherwise, single sign-on will immediately sign the user back in. Alternatively, you can disable sign-out.
Windows Impersonation
Impersonation occurs when an application makes a request as a user instead of as the application—the application impersonates the user. Impersonation ensures that the resource receiving the request knows the identity of the user that originated the request.
For example, in Essentials, when a user prints the map, the viewer sends the print request to Essentials, and Essentials sends a map image request to the map service. Normally, the map image request is made as Essentials. When impersonation is enabled, the map image request is made as the user—Essentials impersonates the user.
To use Windows impersonation:
-
The service must be an ArcGIS Server map service.
-
Both the service and the Essentials site or component must be secured using Integrated Windows Authentication.
-
The end user must be on the domain—impersonation does not work when the user connects over the Internet.
-
The Essentials server must be on the domain.
Allowing Windows impersonation ensures that ArcGIS Server knows the identity of the user that made the request.
For instructions on enabling Windows impersonation, see Global Security Settings.
In addition to impersonating users when connecting to services, Essentials can impersonate users when connecting to data links. If you are using Windows impersonation and your sites use data links, see Data Connections for information.
Configure the Windows Identity Security Provider
To configure the Windows Identity security provider:
-
Windows Authentication must be enabled in IIS.
-
Make sure that the Windows Integrated security provider is enabled.
The Windows Integrated security provider is enabled by default.
-
If you want, edit the security provider to change the name to something that is more meaningful to end users.
-
Configure permissions using the Windows users and roles in each site that you want to secure using the Windows Integrated security provider.
-
If Windows Integrated is the only security provider you are using to secure a site, optionally configure the site's sign-in settings.
To prevent single sign-on from immediately signing a user back in after signing out, you can either configure a landing page or disable sign-out in the site's sign-in settings.
-
If both ArcGIS Server and Essentials are secured using Windows Authentication and ArcGIS Server needs to know user identities, enable Windows impersonation.
-
If you are using Windows impersonation and you also want to use impersonation when connecting to data links, enable impersonation on the data connections.
See also...