Security
The Security feature enables you to control access to your sites and protect your ArcGIS Server map services. You can control access to entire sites, and to individual parts of a site (map services, layers, workflows, reports, and more).
Security is implemented using users, roles, and permissions. To view a secured site, a user must present valid credentials (authenticate) and the user must have permission to access the site (authorize). When a user launches a viewer, the user may have to sign in if the site or any of its sub components are secured.
Security providers store and manage the users and roles that are used for security. Membership providers are security providers that store users. Role providers are security providers that store roles. There are also two special, predefined global roles.
A secured site has at least one permission configured for at least one enabled security provider. It does not matter what the configuration is—the fact that at least one component has a permission set for it means that security is in force.
If you already have users and roles set up for some other purpose besides Essentials, you can configure Essentials to use these existing users and roles. This allows users to authenticate using the same credentials that they already use in some other context. For example, you could configure Essentials to use Windows users and groups.
You can configure more than one security provider. If you apply permissions to a site using more than one security provider, users choose which security provider to sign in with. Signing in with one security provider can give access to different parts of the site than signing in with a different security provider. Viewers have Sign in and Sign out hyperlinks that allow users to sign out of one security provider and sign in using a different security provider.
Security providers are configured globally—all the sites in an instance of Essentials have access to the same security providers. Enforcement of SSL encryption (HTTPS) is also set globally. (Before version 4.0 of Essentials, security providers and SSL were configured within each individual site.)
Manager has a Security Health function that evaluates your security configuration for potential weaknesses. Use the Security Health function to close gaps in your security configuration.
See also...
Functions of Security
The purpose of Essentials Security is to control which users can access your data. Essentials Security has two effects:
-
Filtering: Essentials Security filters which parts of the site users can see. You can prevent users from seeing an entire site, particular map services and layers, or other configured components like charts, reports, and workflows.
-
Layer Security (Proxy): Essentials Security secures communications between the site's ArcGIS Server services and Geocortex viewers. This is done by proxying service requests through Essentials. Instead of seeing the service's URL in the browser's address bar, the user sees the URL of an Essentials endpoint.
Filtering
Filtering allows you to control which parts of a site users see in the viewer. The Filtering function of Essentials Security is useful for hiding parts of a site that are not relevant to the user.
When a user is denied permission to a particular component in a site, that component is not visible in the viewer, it cannot be queried, and it does not appear in map exports, reports, or printouts. For more information about the visibility of secured components, see Permissions.
The Filtering function does not secure components—it does not hide the service's URL from the user. Filtering simply prevents components from appearing in the viewer.
Filtering also prevents unauthorized access to the site's REST API—an unauthorized user cannot view the site's REST endpoints in the REST API Sites Directory, and an unauthorized application cannot access the site programmatically.
Unlike the Layer Security function, filtering works for all the types of service that you can add to the map.
You can exclude layers that you do not want anyone to see. For information, see Exclude Layers from a Dynamic Map Service. If you want some users or applications to be able to access a layer, use the Security feature's filtering capability instead of excluding layers.
Layer Security (Proxy)
The Layer Security function of Essentials Security prevents a malicious user from using Essentials to access your ArcGIS Server services. It does this by proxying requests through Essentials.
As soon as you apply a permission to one layer in the service or you configure a layer filter workflow for one layer, all viewer requests that would previously have gone directly to ArcGIS Server now go through Essentials' built-in Layer Security proxy—the viewer no longer communicates directly with the service, and the user sees the URL of an Essentials REST endpoint instead of the URL of the service. This is illustrated below.
The Layer Security proxy is specific to a map service. If your site has more than one ArcGIS Server map service, each map service with at least one secured layer or layer filter workflow has its own Layer Security proxy.
The Layer Security function works for ArcGIS Server map services, feature services, and image services only. Requests to other types of service, such as WMS services and geocoding services, are not proxied.
If you secure ArcGIS Server using a proxy page and you apply permissions to one or more layers, the Layer Security proxy takes precedence over your proxy page.
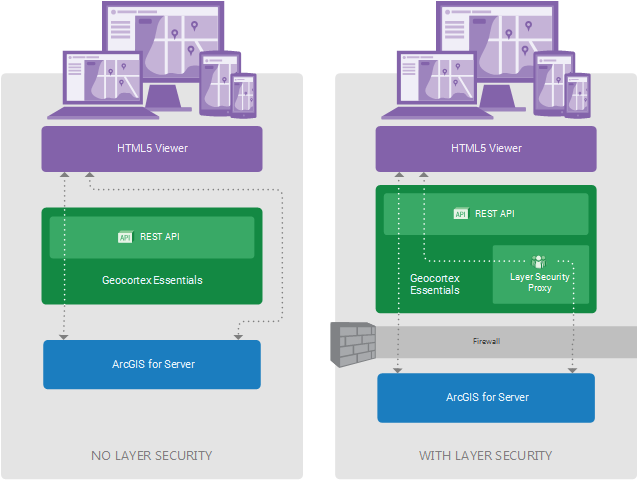
System without Layer Security (left) and with Layer Security (Right)
In the diagram on the left, labelled No Layer Security, viewers request map images and data directly from ArcGIS Server. This is represented by the right-hand arrow bypassing Geocortex Essentials.
The left-hand arrow represents Essentials REST API operations. Certain REST API operations, such as printing, require Essentials to make a request to ArcGIS Server. This is represented by the arrow continuing through Essentials to ArcGIS Server. Essentials can freely make requests to ArcGIS Server as needed, regardless of whether Layer Security is in force. This is why the left-hand arrow is the same in both diagrams.
In the diagram on the right, labelled With Layer Security, viewer requests for map images and data go to the Essentials Layer Security proxy before being forwarded to ArcGIS Server. Responses go back through the proxy.
The ArcGIS Server services must be behind a firewall or otherwise secured. Otherwise, a malicious user could access the services directly, bypassing the Essentials Layer Security proxy.
The diagram has been simplified to show a single Layer Security proxy. This implies a single secured ArcGIS Server map service, because each secured ArcGIS Server map service has its own proxy. In the more general situation, there may be many ArcGIS Server map services, some of which are secured and others not. In this case, there would be many proxies—one for each secured service—and the unsecured services would communicate directly with the viewers.
Main Steps to Set Up Security
The procedure below outlines the main steps to secure Essentials.
To set up Essentials security:
-
SSL: If you do not have a working SSL certificate, get one and install it.
By default, the SSL is enforced in Essentials.
Turning off SSL enforcement is not recommended—SSL encryption is a critical part of a complete security picture.
See SSL Encryption.
-
Security Settings: Configure the security settings.
-
Security Providers: Configure the security provider(s) that you want to use:
-
Sign-In Settings: For each site, configure the settings that control sign-in and sign-out behavior.
See Sign-In Settings.
-
Permissions: For each site and each security provider, apply permissions to users and roles.
See Permissions.
-
Security Health Check: Check for and correct potential weaknesses in your security configuration.
-
Filter Features: If you want to restrict the particular features that different users see, configure feature filtering.
See also...